On Codes and Ciphers; The Imitation Game
“Are you paying attention? Good. If you are not listening carefully, you will miss things, important things. I will not pause, I will not repeat myself, and you will not interrupt me. You think that because you’re sitting where you are and I am sitting where I am, that you are in control of what is about to happen. You’re mistaken. I am in control, because I know things that you do not know.” - The Imitation Game, 2014.
Alan Turing was a revolutionary mathematician, a pioneer among computer scientists and, most importantly, one of the key players in resolving World War II through his immense contribution to the decoding of the Enigma cipher. The Allied forces were in a near-constant state of perplexion over how to crack the Enigma, the cipher used by the Germans, in order to encrypt messages. Though the Enigma was reported to have been decoded by the Polish well before him, Turing’s original method of decrypting the cipher was instrumental in predicting German movements during the War.
The Enigma was believed to be impossible to crack. Ultimately, however, it was broken, bearing testimony to how nothing is truly unbreakable, and every system has a catch attached to it; a principle well highlighted by modern cryptologists like Shamir and Bonhe.
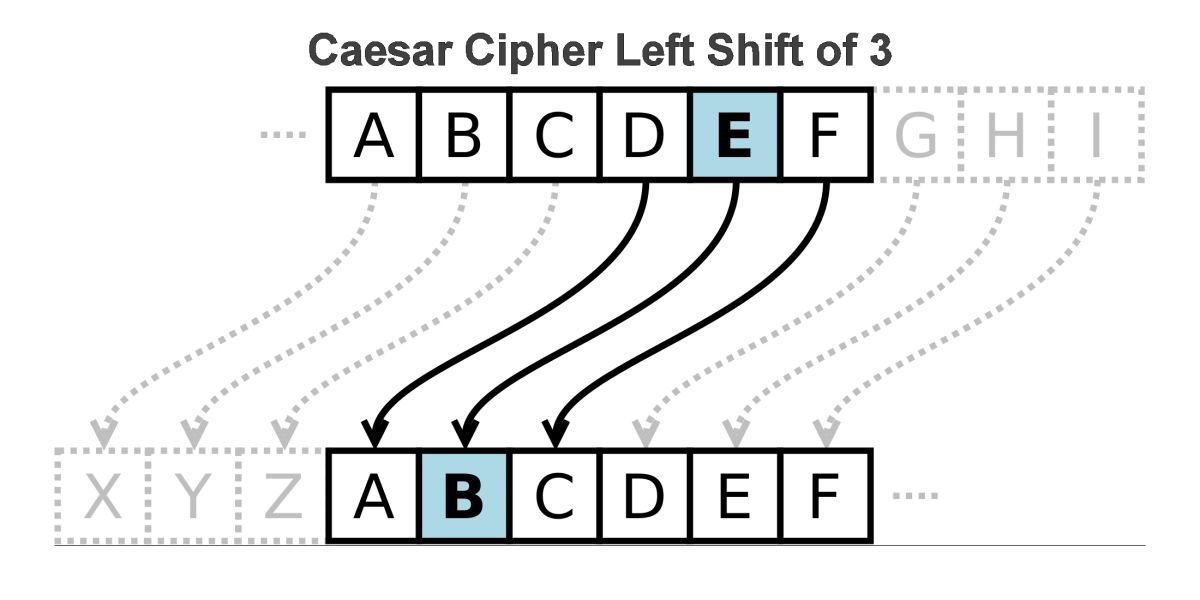
The conceptualisation of codes and ciphers is well-documented alongside the history of warfare and the development of language, as we know it. A very famous cipher, the Caesar Cipher, was supposedly used by the famous Roman general to communicate messages from one camp to another whilst maintaining the authenticity of commands. In the cipher, the first letter of the alphabet is replaced with any chosen letter, the subsequent letters then get replaced in a similar order. For example, in the ‘G Cipher’, A gets replaced by G, B gets replaced by H and so on.
One of the key aspects of codes and ciphers comes from the concept of steganography. Even though steganography is considered to be a part of cryptology, it actually isn’t, it is simply a method of hiding information, using pictures. This method is said to be foolproof. It was even used in the very famous or rather infamous case of Cicada 3301, when an unknown group of people claimed to hide information within certain images, and challenged someone to crack it.
Another prominent cipher is the Vigenere Cipher; a key-controlled Caesar Cipher. A key is a system through which one can encode or decode anything, like messages or warnings. Vigenere Ciphers have been instrumental during war communication even during the era of the Napoleonic Wars and have stood the test of time, being one of the most recognisable of ciphers today. However, the claim to the throne of the most illustrious cipher would, undisputedly, go to the Morse Code. The concept behind the Morse Code, (which despite the misnomer of being a code, is actually a cipher) is also behind the invention of the telegraph by, you guessed it, Samuel Morse.
For almost half a century, the Telegraph was the only means by which electronic messages could be sent and received. The Morse Code expresses words, i.e. the letters and numbers that constitute them, in the form of ‘dots and dashes’ and it is in this form that it is sent to the receiver. Morse Code, however, has been, quite interestingly, used in several other forms such as taps and untaps; tapping signifying a dot, and pausing a dash. (Yes, Sherlock fans, you guessed it, didn’t you)? The Morse Code is quite a reliable form of masking data, if masked properly that is.
Funny enough, codes and ciphers have been an integral part of artistic movements in Europe. One of the most renowned ciphers was developed by one of the most talented men in Europe. Although his name is obscure, he is considered to have talent comparable to the likes of Leonardo Da Vinci. Most of the relics of that age have been protected using this very cipher. The cipher in question is the Alberti Cipher, conceptualised by the revolutionary, Alberti. This cipher replaces words according to a disk which helps encrypt and decrypt the text.
The famous author David Kahn notes in his book The Codebreakers that history has forgotten several of the other famous ciphers, such as the ones used by many mathematicians in the Middle-East during the Oriental age, the Scytale Cipher used by the Spartans during their Golden Age, and so on. There has been no dearth in the human ability to innovate. In order to create a foolproof cipher system, all has been done, ranging from methods of transposition (that is to replace one word with another, as was utilised by the famous Gronsfeld Cipher) to the generation of intelligent schemes to make decryption difficult without the key.
However, when the Enigma was built, it was almost as if the pinnacle of human comprehension was reached and it was presumed that it could not be broken, no matter what the Allies did. However, a group of people in Bletchley Park refused to give up and the rest, as they say, is history. Alan Turing has been an inspiration for the greatest of modern cryptographers, from Adi Shamir to Malcolm Williamson. In an age in which it is predicted that computers might rule the world, the authenticity of information and security are some of the biggest concerns. Cryptography and its application are only going to get more complex and esoteric, to the extent that we may not be able to comprehend even abstract concepts on the quantum nature of information.
Information, they say, is key. The philosophy behind the establishment, setting up and the consequent breaking of codes signifies the ultimate nature of how we are. It signifies the essence of humankind. It is in the nature of man to build and then eventually destroy, to construct and then ultimately deconstruct, only for a better possibility to be explored. Human nature tells us that nothing is truly unbreakable and that everything, which is part of human effort, can be brought down, thanks to humans themselves.
Codes help us express ourselves in a niche manner, truly being an indication of the creativity and perseverance, we as humans, are able to display and put into effect.
Subscribe to The Pangean
Get the latest posts delivered right to your inbox